I have a CGI script that works fine with the built-in HTTP server (run as python -m http.server --cgi). However, when I try to use the same CGI handler in a server that supports HTTPS, I get a TLSV1_ALERT_RECORD_OVERFLOW.
I have not been able to find any information about what this error is or what it might mean. I can’t find any examples of Python’s CGI being used over HTTPS either, so I don’t even know if they can be used together.
This is the CGI script that I’m trying to run:
#!/bin/bash
inotifywait --event modify .
echo Content-type: text/plain
echo
echo Watched file modified
This is the error the server throws:
127.0.0.1 - - [05/Feb/2023 16:30:49] "GET /cgi-bin/inotifywait HTTP/1.1" 200 -
----------------------------------------
Exception occurred during processing of request from ('127.0.0.1', 57506)
Traceback (most recent call last):
File "/usr/lib64/python3.10/socketserver.py", line 683, in process_request_thread
self.finish_request(request, client_address)
File "/usr/lib64/python3.10/socketserver.py", line 360, in finish_request
self.RequestHandlerClass(request, client_address, self)
File "/usr/lib64/python3.10/http/server.py", line 651, in __init__
super().__init__(*args, **kwargs)
File "/usr/lib64/python3.10/socketserver.py", line 747, in __init__
self.handle()
File "/usr/lib64/python3.10/http/server.py", line 425, in handle
self.handle_one_request()
File "/usr/lib64/python3.10/http/server.py", line 413, in handle_one_request
method()
File "/home/lunariel/.local/lib/python3.10/site-packages/uploadserver/__init__.py", line 219, in do_GET
else: http.server.CGIHTTPRequestHandler.do_GET(self)
File "/usr/lib64/python3.10/http/server.py", line 655, in do_GET
f = self.send_head()
File "/usr/lib64/python3.10/http/server.py", line 993, in send_head
return self.run_cgi()
File "/usr/lib64/python3.10/http/server.py", line 1158, in run_cgi
if not self.rfile.read(1):
File "/usr/lib64/python3.10/socket.py", line 705, in readinto
return self._sock.recv_into(b)
File "/usr/lib64/python3.10/ssl.py", line 1274, in recv_into
return self.read(nbytes, buffer)
File "/usr/lib64/python3.10/ssl.py", line 1130, in read
return self._sslobj.read(len, buffer)
ssl.SSLError: [SSL: TLSV1_ALERT_RECORD_OVERFLOW] tlsv1 alert record overflow (_ssl.c:2548)
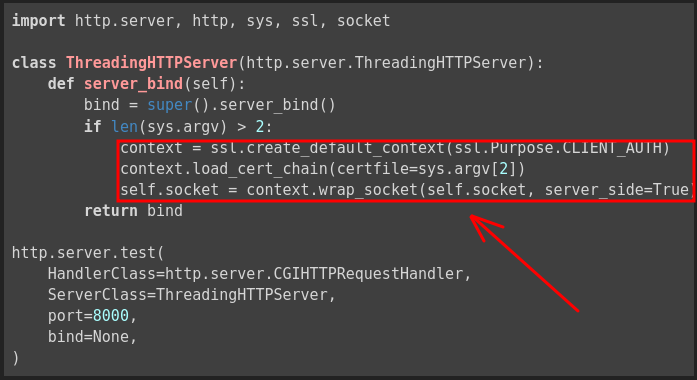
This is a minimal server that reproduces the issue (run with no arguments and it serves HTTP and the CGI works, pass a .pem file in and it uses HTTPS and the CGI fails):
import http.server, http, sys, ssl, socket
class ThreadingHTTPServer(http.server.ThreadingHTTPServer):
def server_bind(self):
bind = super().server_bind()
if len(sys.argv) > 2:
context = ssl.create_default_context(ssl.Purpose.CLIENT_AUTH)
context.load_cert_chain(certfile=sys.argv[2])
self.socket = context.wrap_socket(self.socket, server_side=True)
return bind
http.server.test(
HandlerClass=http.server.CGIHTTPRequestHandler,
ServerClass=ThreadingHTTPServer,
port=8000,
bind=None,
)
I tried removing the inotifywait call and using a CGI script that just sent a text string, but that had the same error. The server is able to server regular files (.html, .js, etc.) over HTTPS, so I don’t think it’s a certificate issue.